CertExams.com Simulator Lab Exercises Answers
Description: Lab exercise explains configuration and verification of policy based vpn
Network Diagram:
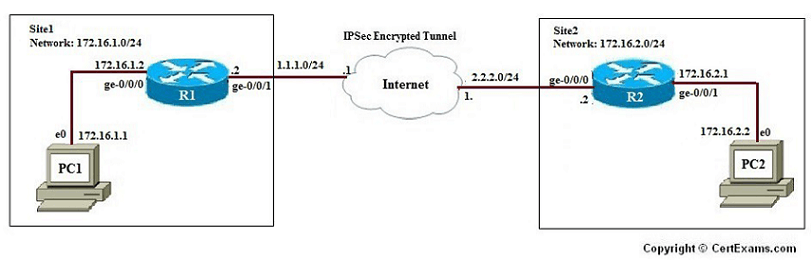
Instructions:
I. Configuration on site1 on device R1
1. Configure the Ethernet interface ip address
2. Configure the default route
3. Configure security zones, and assign interfaces to the zones
4. Configure host-inbound services for each zone. Specify allowed system services for the security zone.
5. Configure address book entries for each zone.
6. Configuring IKE Phase1 proposals
7. Configure IKE Phase 1 policies and reference the IKE proposals
8. Configure the IKE Phase 1 gateway and reference the IKE policy configured in Step 7
9. Configuring IPSEC Phase 2 Proposals
10. Configure the IPSEC Phase 2 policies and reference the IPSEC proposals
11. Configure the IPSEC Phase 2 VPN tunnel and reference the IPSEC Phase 2 policy configured in Step 10
12. Create the policies to define the interesting traffic
I. Configuration on Site2 (on device R2)
1. Configure the Ethernet interface ip address
2. Configure the default route
3. Configure security zones, and assign interfaces to the zones
4. Configure host-inbound services for each zone.
5. Configure address book entries for each zone.
6. Configuring IKE Phase1 proposals
7. Configure IKE Phase 1 policies and reference the IKE proposals
8. Configure the IKE Phase 1 gateway and reference the IKE policy configured in Step 7
9. Configuring IPSEC Phase2 Proposals
10. Configure the IPSEC Phase 2 policies and reference the IKE proposals
11. Configure the IPSEC Phase 2 VPN tunnel and reference the IPSEC Phase 2 policy configured in Step 10
12. Create the policies to define the interesting traffic
Please refer to the CertExams.com Juniper Network Simulator softwarefor complete lab.