CertExams.com Simulator Lab Exercises Answers
Description: First, you configure one or more IKE proposals; then you associate these proposals with an IKE policy. You can also prioritize a list of proposals used by IKE in the policy statement by listing the proposals you want to use, from first to last.
The lab exercise explains the IKE phase1 proposal configuration for a VPN tunnel
Command Syntax:
[edit security ike]
user@srx#show
proposal <proposal-name>{
authentication-method [pre-shared-keys | rsa-signatures];
dh-group [group1 | group2 | group5];
authentication-algorithm [md5 | sha-256 | sha1];
encryption-algorithm [3des-cbc | aes-128-cbc | aes-192-cbc | aes-256-cbc | des-cbc];
lifetime-seconds <seconds>;
}
Network Diagram:
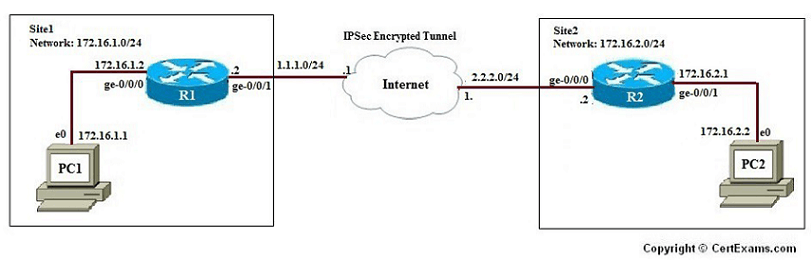
Instructions:
1. Create the ike phase1 proposal
2. Define the IKE proposal authentication method.
3. Define the IKE proposal Diffie-Hellman group.
4. Define the IKE proposal authentication algorithm.
5. Define the IKE proposal encryption algorithm.
Please refer to the CertExams.com Juniper Network Simulator software for complete lab.