Description: This exercise helps to know about various security threats.
Instructions :
1.Various Security threats are given on the column A
2.Their features are given on the column B
3. Match (drag and drop) the Security threat given on Column A with their appropriate feature given on the column B.
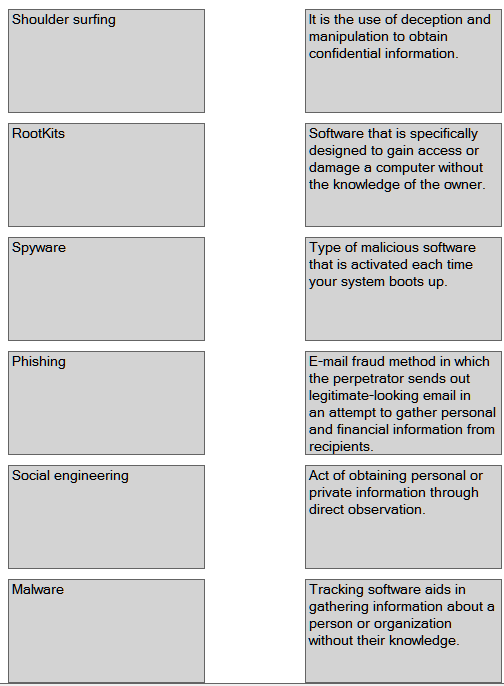
Explanation:
Social Engineering: Social engineering is a process in which an attacker attempts to acquire information about your network and system by social means, such as by talking to people in the organization. Social engineering is grouped into three methodologies:
1. Phishing: The practice of sending emails appearing to be from reputable sources with the goal of influencing or gaining personal information.
2. Vishing: The practice of eliciting information or attempting to influence action via the telephone, may include such tools as “phone spoofing”.
3. Impersonation: The practice of pre-texting as another person with the goal of obtaining information or access to a person, company, or computer system.
Malware: "Malware" is a term for any software that gets installed on your machine and performs unwanted tasks, often for some third party's benefit. Malware programs can range from being simple annoyances (popup advertising) to causing serious computer invasion and damage (e.g., stealing passwords and data or infecting other machines on the network). Additionally, some malware programs are designed to transmit information about your Web-browsing habits to advertisers or other third party interests, unbeknownst to you.
Rootkits: A rootkit is a collection of tools (programs) that enable administrator-level access to a computer or computer network. Typically, a cracker installs a rootkit on a computer after first obtaining user-level access, either by exploiting a known vulnerability or cracking a password. Once the rootkit is installed, it allows the attacker to mask intrusion and gain root or privileged access to the computer and, possibly, other machines on the network.
Phising: The act of sending an email to a user falsely claiming to be an established legitimate enterprise in an attempt to scam the user into surrendering private information that will be used for identity theft. Phishing email will typically direct the user to visit a website where they are asked to update personal information, such as a password, credit card, social security, or bank account numbers, that the legitimate organization already has. The website, however, is bogus and will capture and steal any information the user enters on the page.
Shoulder surfing: Shoulder surfing is using direct observation techniques, such as looking over someone's shoulder, to get information. Shoulder surfing is an effective way to get information in crowded places because it's relatively easy to stand next to someone and watch as they fill out a form, enter a PIN number at an ATM machine, or use a calling card at a public pay phone. Shoulder surfing can also be done long distance with the aid of binoculars or other vision-enhancing devices.
Spyware: Spyware is any technology that aids in gathering information about a person or organization without their knowledge. On the Internet (where it is sometimes called a spybot or tracking software), spyware is programming that is put in someone's computer to secretly gather information about the user and relay it to advertisers or other interested parties. Spyware can get in a computer as a software virus or as the result of installing a new program.
Cert-Ex™ Exam Simulators, Cert-Ex™ Network Simulator, Cert-Ex™ Cheatsheets are written independently by CertExams.com and not affiliated or authorized by respective certification providers. Cert-Ex™ is a trade mark of CertExams.com or entity representing Certexams.com.A+™ is a trademark of CompTIA® organization.